AI Enhanced Fraud, otherwise known as Deepfake or Social Engineering Attack is reaching epidemic levels across the world and not only has the potential to create financial havoc but even has the potential to destabilize governments.
While Deepfake Voice and Video AI inference models (that analyze video and voice streams to see if Deepfake) are helpful, they are just a small piece of the puzzle. A bigger piece of the puzzle and therefore a better tool against AI Enhanced Fraud is to aggregate the Metadata from all forms of communication to provide shared awareness to help recognize people. When you recognize a friend or a coworker…no trust is needed, it is already inherent.

netarx believes that the only way to defeat AI Enhanced Fraud is to use every tool, in every arsenal, to provide this shared awareness. It is why we developed the Flurp.
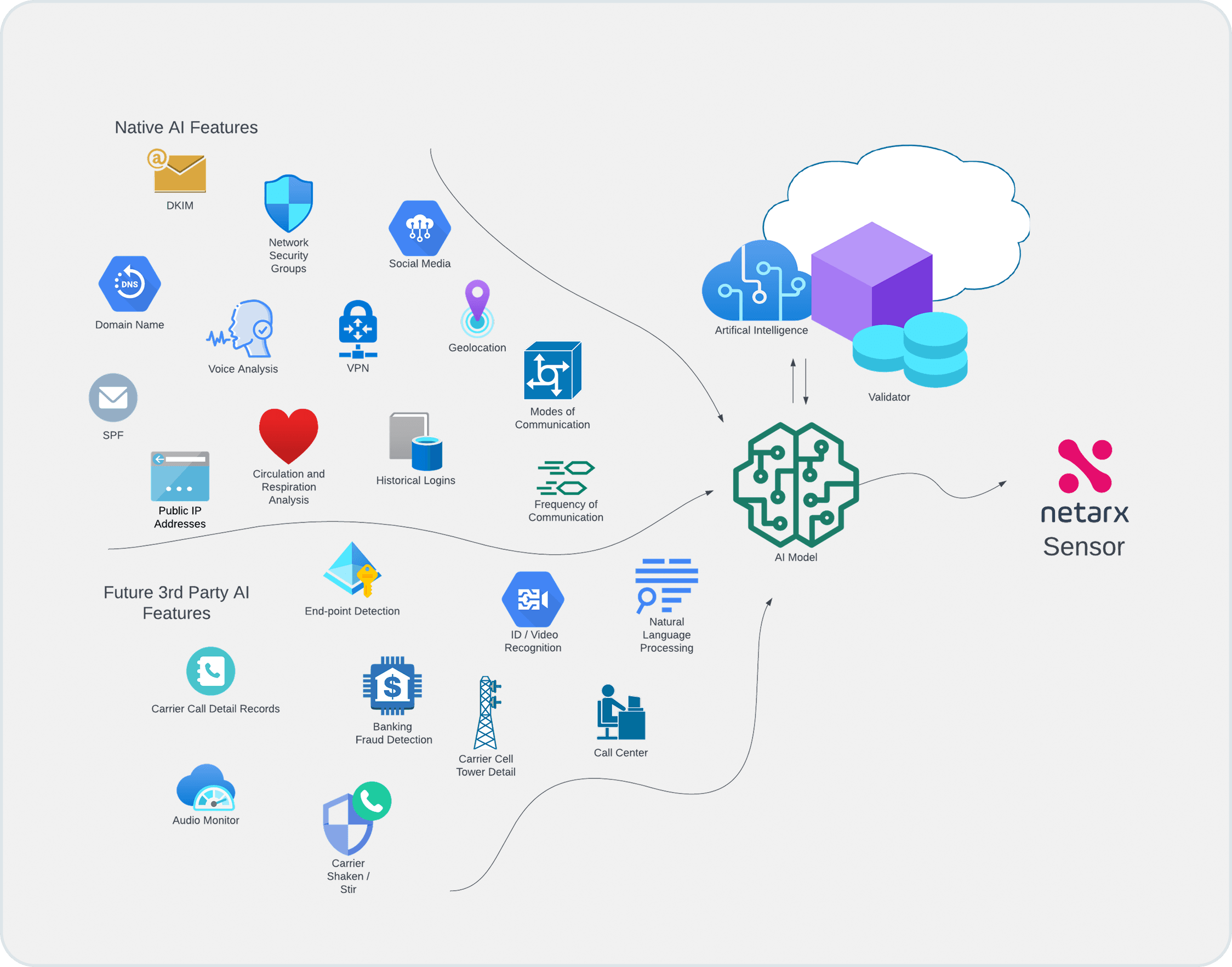
The Flurp aggregates metadata from many different sources of communication.
All this metadata is organized into different features and AI inference Models. Some features are used as inputs in AI Supervised Learning. Other Features are used by Deep Learning or Unsupervised Learning. In fact, the same metadata can be used by both supervised and unsupervised.
Let’s look at GPS as an example:
If we look at GPS metadata from potentially dangerous countries, we can train a Supervised Learning model to report on potentially higher risk communication, such as communication from North Korea.
Alternatively we can use GPS coordinates as features in an Unsupervised Learning model for anomaly detection or in other words, unusual movements or patterns that don’t fit past behavior, such as communication from a user in one part of the world and then an hour later over 5000 miles away from the original location.

The Netarx Flurp has over 75 features aggregated into various AI Models that funnel into a voting ensemble. We are constantly incorporating more metadata and creating new AI models so you can continue to recognize friends or co-workers in an ever more threatening world. In addition to our proprietary elements, some additional examples include:
SPF/DKIM
DMARC
Calendar/Participant ID
Device ID
Calling/Called Party
Time/Date