In a hyper-connected world, the nIn a hyper-connected world, the need to analyze data across organizational and jurisdictional boundaries is critical. However, centralizing sensitive information into a single repository creates significant privacy risks, compliance challenges, and security vulnerabilities. A federated data model provides an advanced solution, enabling secure analysis and insight generation on decentralized data without ever moving or pooling it. This approach allows organizations to collaborate and enhance security awareness while maintaining strict control over their proprietary information.

Traditional data analysis requires aggregating data into a central location, which is often unfeasible due to data sovereignty laws (like GDPR), privacy concerns, or intellectual property considerations. Federated data architecture circumvents these barriers. It brings the analysis to the data, not the other way around. This allows multiple entities to contribute insights from their datasets for a collective benefit, such as improved threat detection, without exposing the raw data itself.
Enhanced Data Privacy and Security:
Sensitive data remains within its secure, local environment. Only insights, not the underlying information, are shared. This fundamentally minimizes the risk of data breaches during transit or from a compromised central repository.
Compliance with Data Sovereignty Regulations:
Organizations can adhere to strict data residency and privacy laws (e.g., GDPR, CCPA) by keeping data within its required geographical or network boundaries. This is crucial for multinational operations and for sectors like healthcare and finance.
Secure Cross-Organizational Collaboration:
Enables different companies, departments, or partners to collaborate on threat analysis. For instance, multiple financial institutions can collectively identify a widespread phishing campaign by sharing anonymized attack patterns, without revealing specific customer data.
Maintained Control Over Proprietary Data:
Each participating entity retains full ownership and control of its data. You decide what information is used for analysis and what insights are shared, ensuring that your intellectual property and confidential information are protected.
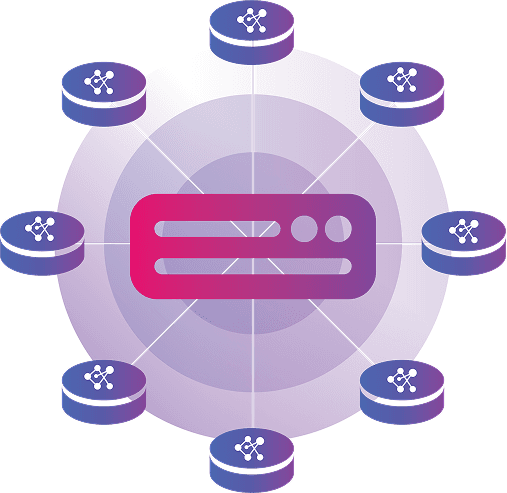
Our platform utilizes a federated approach to deliver comprehensive insights while respecting the security and privacy of each data source. The system is designed to perform analysis locally and then aggregate the results in a secure, anonymized fashion.
Local Analysis Nodes:
The system deploys lightweight analysis nodes within each participant's environment. These nodes have secure access to local data sources for processing.
Decentralized Processing:
When an analytical query is initiated (e.g., "identify patterns related to a new malware variant"), the central orchestrator sends the analysis model—not a request for data—to each local node.
On-Site Computation:
Each node executes the analysis locally on its own dataset. This computation generates anonymized, aggregated results or model updates. The raw data never leaves its secure perimeter.
Secure Aggregation of Insights:
The anonymized results from each node are sent back to a central aggregator. This component combines the insights from all participants to create a comprehensive, high-level model or report. This collective intelligence provides a more complete picture than any single organization could achieve alone.